Ambit Core: Post-Quantum Networking for Data Centers
Summary
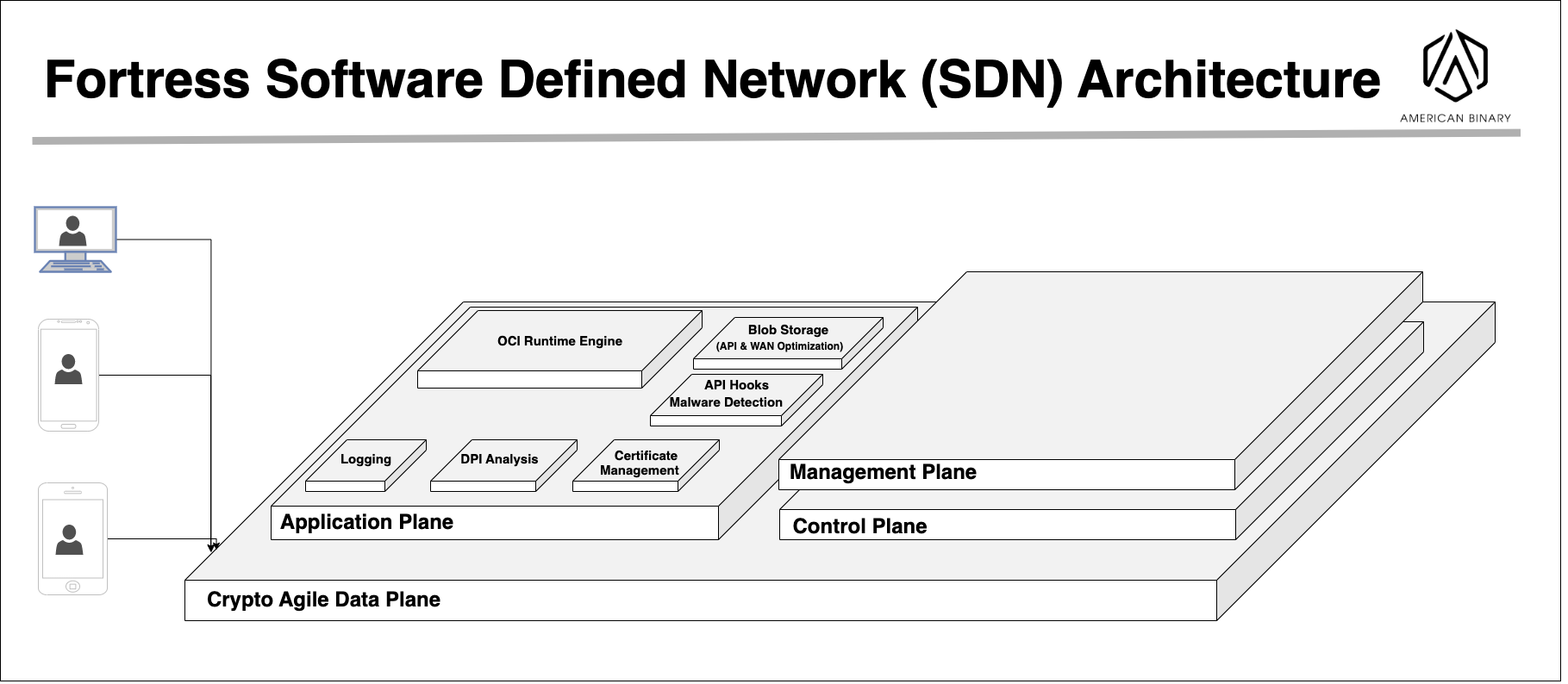
Ambit Core is a maximally secure and efficient software defined network that leverages Kubernetes with a Vector Packet Processing data plane for the Data Link, Network, and Transport layers; all plus the Application layer support Post-Quantum encryption.
High customization and scalability is built-in from the ground up, thanks to an open architecture, Kubernetes, and Ansible. New servers can be deployed in minutes. Configurable for various use cases; the application plane can run any number of diverse workloads. Feauturing Crypto-Agility, all data transmitted across the network is compliant with today's requirements and Post-Quantum Encryption can be effortlessly deployed when ready. Ambit Core's architecture enables transparency and granular control of the network, enhancing efficiency and reducing operational costs.
Sleep easy knowing your network is as secure and efficient as possible - choose Ambit Core.
Get the White Paper
Benefits
- Get a larger ROI on existing hardware
- Reduce management costs through automation
- Transition to Post-Quantum encryption at no extra charge
- Rapidly scale across multiple clouds, edge servers, and even on-prem white-boxes, line cards, and more
- Effortlessly use the best DevSecOps and/or Platform Engineering practices
- Run any number of diverse workloads
- Upgrade effortlessly to state-of-the-art cryptography expected to last for decades
- Ensure compliance with existing and future standards
- Use any standardized network protocol
- Identify problems, their root causes, and solutions easily
- Application Awareness and Deep Packet Inspection allows better detection of security issues
- Reduce management burden through automation
Features
It works by using a ML-KEM 1024 static key along with a ML-KEM 512 ephemeral key.
Be compliant today with US Federal standards while being prepared for a seamless transition to Post-Quantum Encryption when standards change.
- Multi-factor authentication
- Single Sign On (SSO) through SAML, Active Directory/LDAP, OAuth
- Modular enough to facilitate any other authentication scheme that an organization requires.
- Application aware
- Natively embeds “runc” allowing deployment of OCI Containers, such as Docker.
- Deploys a Restful Blob storage engine
- API compatible with S3.
- Revision control built into the filesystem– can automatically roll back in the event of disaster/malware infection.
- Can retrieve files on a delta basis, facilitating WAN Optimization saving bandwidth
- Deploy powerful APIs across your enterprise to leverage best-in-class third party Anti-Malware solutions
- Get Metrics from your Anti-Malware platform to ensure compliance and security
- SDK available for third-party developers (soon)
- Native built-in Certificate Management
- Facilitate crypto-agile x509 certificates (soon)
- Can integrate with any other valid Certificate Authority
Frequently Asked Questions
Post-quantum encryption refers to encryption methods that are secure against an attacker with a quantum computer. Current encryption methods, such as RSA and Elliptic Curve Cryptography (ECC), are vulnerable to quantum computers (cryptographically relevant quantum computers) and could potentially be broken by them. Post-quantum encryption is important because it ensures the security of encrypted communications even against a quantum computing attack. It is important to care about post-quantum encryption because it can protect sensitive information from being compromised in the future as quantum computing technology advances.
Being crypto-agile refers to the ability to quickly and easily adapt to changes in cryptographic methods and
technologies. This includes the ability to upgrade encryption algorithms and protocols as new weaknesses are
discovered or new technologies become available. It also includes the ability to switch between different
algorithms or protocols as needed to ensure continued security.
Crypto-agility is important because it allows organizations to maintain the security of their communications and
protect sensitive information even as cryptographic threats evolve. It enables organizations to respond to new
vulnerabilities and attacks by quickly deploying new cryptographic methods, rather than waiting for a complete
system overhaul.
Adopting a crypto-agile approach can also help organizations avoid vendor lock-in and maintain flexibility in
their security strategies.
The National Institute of Standards and Technology (NIST) is concerned about Elliptic Curves, Diffie-Hellman
(DH), Elliptic Curve Diffie-Hellman (ECDH), and RSA (Rivest–Shamir–Adleman) because they are all vulnerable to
quantum computing attacks. Quantum computers can potentially use algorithms such as Shor's algorithm to break
the encryption used by these methods, which would allow an attacker to access sensitive information that was
thought to be secure.
In 2016, NIST launched a process to identify new post-quantum cryptography standards and algorithms that will be
more secure against quantum computing attacks than existing standards. The goal of this process is to develop
and standardize new cryptographic methods that will be secure against both classical and quantum computing
attacks, and will replace the existing standards that are vulnerable to quantum computing.
Given the recent progress in quantum computing, NIST is concerned that it is important to start the process of
transitioning to post-quantum cryptography now to ensure that sensitive information remains secure in the
future.
The benefits of post-quantum encryption are:
Security against quantum computing attacks: Post-quantum encryption methods are designed to be secure against
attacks from quantum computers, which can potentially break current encryption methods such as RSA and Elliptic
Curve Cryptography (ECC).
Long-term security: As quantum computing technology continues to advance, post-quantum encryption methods will
provide ongoing security for sensitive information, protecting it from future attacks.
Compatibility: Post-quantum encryption methods can be designed to work with current systems and infrastructure,
making the transition to post-quantum encryption more seamless.
Flexibility: Post-quantum encryption methods can offer different levels of security, depending on the specific
use case and the level of protection required.
Encourage innovation: The development of post-quantum encryption methods can encourage innovation in the field
of cryptography, leading to the discovery of new and more secure methods.
Compliance: Some countries and industries have or will require the use of post-quantum encryption methods, so it
would be beneficial to be ready and in compliance.
It Depends on your use-case. Deployment can happen as quickly as a few hours to several months. The use-case determines the deployment time. Please feel free to reach out to us for more information.