AMERICAN BINARY
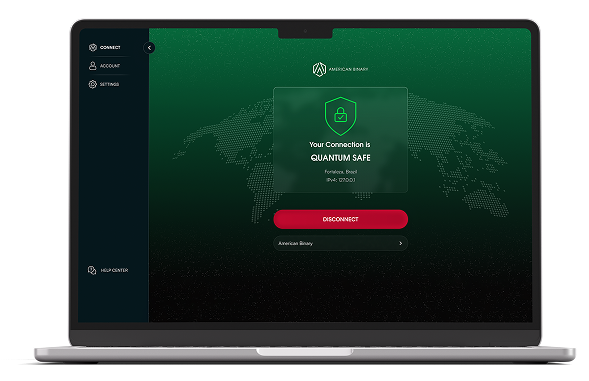
Quantum-Secure VPN
and tunnels
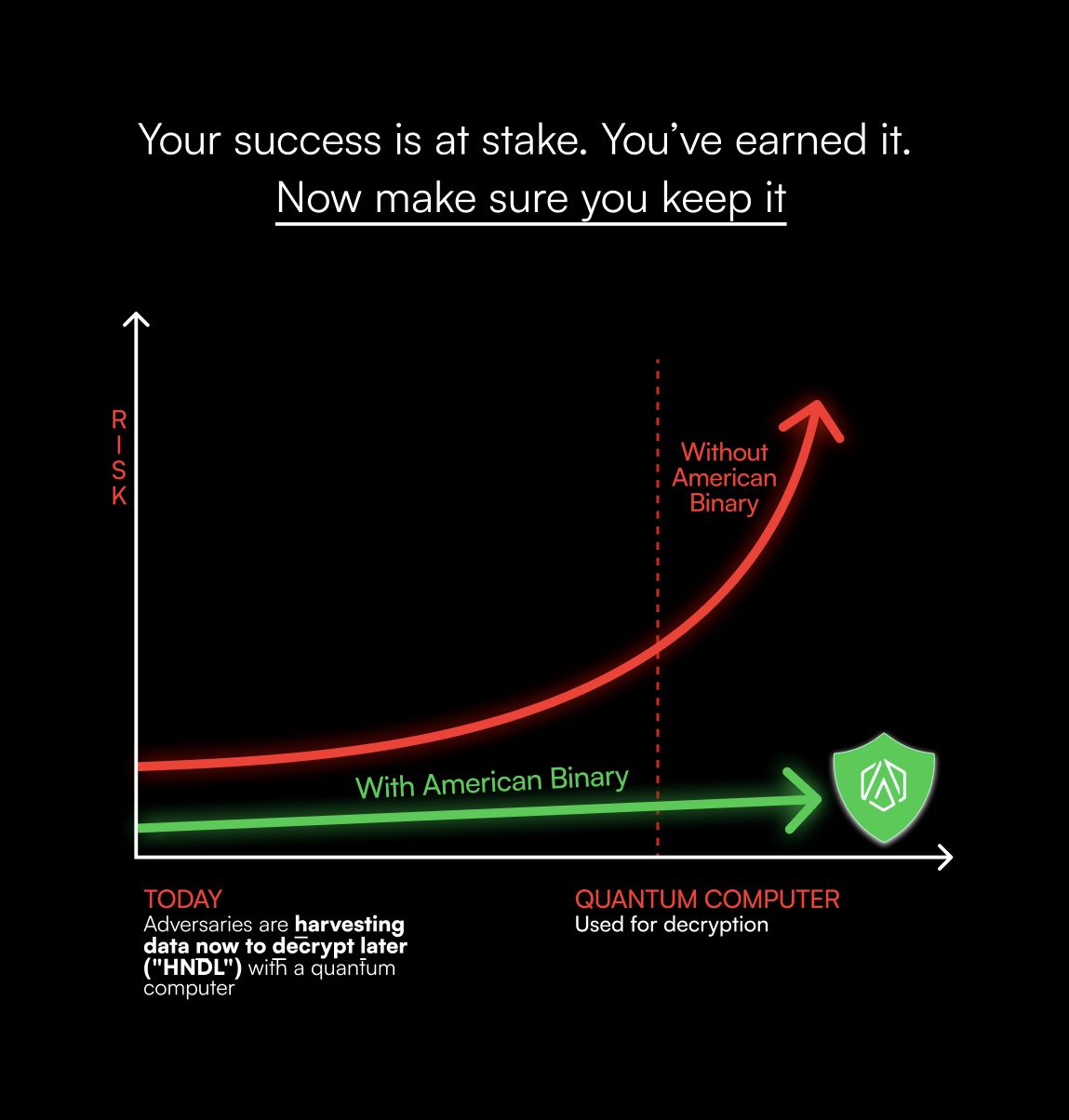
Defense-grade digital armor to protect your livelihood
Defense-grade digital armor to protect your livelihood. Keep what you've earned, with the last VPN you'll ever need.
Keep what you've earned, with the last VPN you'll ever need

"The easiest, least painful security product install. It just worked"
- Anastasia M, CEO
"Part of the minority not selling snake oil"
- Exec, Top CSP
"It took minutes - what are you waiting for!"
- Terry R, CEO